Breaking Down the Science Behind Quantum Encryption Protocols
Step into the fascinating world of quantum encryption, where science meets security in a mind-bending dance of particles and protocols. Quantum mechanics, entanglement, and cutting-edge technology come together to revolutionize data protection like never before. Get ready to unravel the mysteries behind quantum encryption protocols as we delve into this innovative realm where the future of cybersecurity is being reshaped!
The Basics of Quantum Mechanics
Quantum mechanics, the foundation of quantum encryption, delves into the behavior of particles at a subatomic level. It challenges our classical understanding of physics by introducing principles like superposition and entanglement.
In this fascinating realm, particles can exist in multiple states simultaneously until measured, unlike classical bits that are strictly 0 or 1. This allows for unprecedented levels of security in data transmission through quantum encryption protocols.
Entanglement is another mind-boggling concept where two particles become interconnected regardless of distance. Any change to one particle instantaneously affects its entangled partner – a phenomenon exploited in creating unhackable communication channels.
By harnessing these fundamental principles, quantum mechanics enables the development of unbreakable encryption methods that have the potential to revolutionize cybersecurity as we know it.
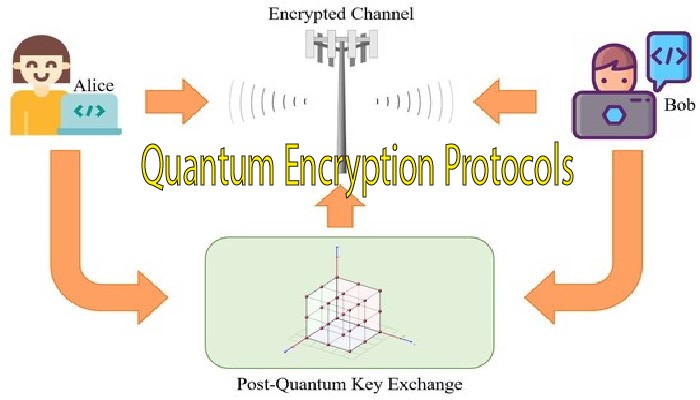
Utilizing Quantum Entanglement for Security
Quantum entanglement, a phenomenon where particles become interconnected and can influence each other regardless of distance, is at the heart of revolutionary security measures. Imagine two particles that are so intricately linked that any change in one instantaneously affects the other, no matter the separation between them. This property forms the basis for unbreakable encryption protocols that leverage quantum entanglement to safeguard data like never before.
By utilizing quantum entanglement for security purposes, cryptographic keys can be generated with unparalleled levels of randomness and complexity. The beauty lies in the fact that any attempt to intercept or eavesdrop on these keys would disrupt their delicate entangled state, alerting parties to potential breaches instantly.
This cutting-edge approach not only ensures secure communication channels but also paves the way for a new era of cybersecurity where traditional hacking methods fall short against quantum-protected systems. The utilization of quantum entanglement as a cornerstone for security marks a significant leap forward in safeguarding sensitive information from malicious threats.
Types of Quantum Encryption Protocols
When it comes to quantum encryption protocols, there are several types that play a crucial role in securing sensitive information. One common protocol is Quantum Key Distribution (QKD), which uses quantum mechanics principles to create secure keys for encrypting data. Another type is Quantum Cryptography, which leverages quantum properties to ensure the confidentiality and integrity of communication.
Furthermore, we have Quantum Teleportation Protocol, which enables the transfer of quantum information between distant locations without physically sending particles. Additionally, researchers are exploring Post-Quantum Cryptography as a way to prepare for future advancements in quantum computing that could potentially break traditional encryption methods.
Each type of quantum encryption protocol has its unique strengths and applications, contributing to the evolving landscape of cybersecurity in the digital age.
Advantages and Challenges of Quantum Encryption
When it comes to quantum encryption protocols, there are both advantages and challenges that come into play. One significant advantage is the unparalleled level of security offered by quantum encryption. Unlike traditional encryption methods, quantum encryption relies on the principles of quantum mechanics, making it virtually impossible for hackers to intercept or decipher secure communications.
On the flip side, one of the main challenges with implementing quantum encryption is its complexity and high cost. Building and maintaining a quantum communication infrastructure requires cutting-edge technology and expertise, which can be a barrier for widespread adoption. Additionally, ensuring compatibility between different systems using quantum encryption can pose interoperability issues.
Despite these challenges, the potential benefits of quantum encryption in safeguarding sensitive data make overcoming these hurdles worthwhile for organizations looking to enhance their cybersecurity defenses in an increasingly digital world.
Real-World Applications and Implementations
Quantum encryption protocols are not just theoretical concepts confined to laboratories; they have practical applications in the real world. One notable use is in secure communication, where sensitive information needs protection from hackers. By leveraging the principles of quantum mechanics, these protocols ensure that data remains confidential and tamper-proof during transmission.
Another exciting application is in banking and financial sectors, where secure transactions are paramount. Quantum encryption adds an extra layer of security to online payments and digital currency exchanges, safeguarding against cyber threats and ensuring safe monetary transactions.
Additionally, quantum encryption technology finds its place in government communications for classified information exchange. The robust security measures provided by quantum protocols make it challenging for unauthorized parties to intercept or decipher sensitive data shared between agencies.
Moreover, industries like healthcare can benefit from quantum encryption to protect patient records and medical research findings from being compromised. The implementation of this advanced form of encryption ensures confidentiality and integrity in handling vital healthcare data.
The widespread adoption of quantum encryption protocols across various sectors highlights their significance in enhancing cybersecurity measures globally. As technology continues to evolve rapidly, exploring further practical applications will undoubtedly pave the way for a more secure digital future.
Future Developments and Possibilities
As we look ahead to the future of quantum encryption protocols, the possibilities are both exciting and vast. Researchers and scientists are continuously working on advancing the field to enhance security measures in an increasingly digital world.
One area of focus is on developing even more sophisticated quantum key distribution methods that can withstand potential attacks from quantum computers. By harnessing the power of quantum entanglement and superposition, these advancements aim to create unbreakable encryption keys.
Furthermore, there is a growing interest in exploring post-quantum cryptography solutions that can withstand attacks not only from conventional computers but also from potential future quantum adversaries. This involves researching new encryption algorithms that can resist threats posed by evolving technologies.
Additionally, with the rise of quantum computing capabilities, there is a need for continued research into enhancing the scalability and efficiency of quantum encryption protocols. This includes optimizing hardware components and streamlining processes to make them more practical for widespread implementation.
The future developments in quantum encryption hold immense promise for bolstering cybersecurity measures and safeguarding sensitive information in an ever-evolving digital landscape.
Conclusion:
In a world where data security is more crucial than ever, quantum encryption protocols offer a promising solution to safeguarding sensitive information. By harnessing the power of quantum mechanics and exploiting phenomena like entanglement, these protocols provide a level of security that surpasses traditional encryption methods.
As technology continues to advance and the need for secure communication grows, the development and implementation of quantum encryption protocols will play a vital role in ensuring data privacy and integrity. With ongoing research and advancements in this field, we can expect even more robust and efficient quantum encryption solutions to emerge in the future.
The potential applications of quantum encryption are vast, ranging from secure communications networks to protecting financial transactions and sensitive government data. As we look ahead to what lies beyond, it’s clear that quantum encryption will continue to be at the forefront of cybersecurity innovation, paving the way for a safer digital landscape for generations to come.