Safeguarding the Digital Frontier: Cybersecurity Threats and Solutions
We are going to discuss about Cybersecurity Threats and Solutions. In today’s interconnected world, where digital technologies pervade every aspect of our lives, cybersecurity has become paramount. As organizations and individuals alike rely increasingly on digital platforms for communication, commerce, and collaboration, the threat landscape continues to evolve, presenting new challenges and vulnerabilities. This article delves into the realm of cybersecurity, exploring the various threats faced by individuals and organizations and examining proactive solutions to mitigate these risks.

Understanding Cybersecurity Threats
- Cybercrime: The Pervasive Threat
Cybercrime encompasses a broad range of malicious activities perpetrated by cybercriminals, including phishing attacks, malware infections, ransomware, and identity theft. These threats target individuals, businesses, and government agencies alike, aiming to steal sensitive information, disrupt operations, and extort financial gain.
- Advanced Persistent Threats (APTs)
APTs are sophisticated, targeted attacks launched by well-funded and organized threat actors, such as nation-state actors or cybercriminal groups. These attacks often involve prolonged reconnaissance and stealthy infiltration of networks, aiming to exfiltrate sensitive data, sabotage infrastructure, or conduct espionage.
- Insider Threats
Insider threats pose a significant risk to organizations, as malicious insiders with authorized access to sensitive systems and data can exploit their privileges to commit fraud, sabotage operations, or steal intellectual property. Insider threats may stem from disgruntled employees, negligent staff, or unwitting accomplices manipulated by external actors.
- IoT Vulnerabilities
The proliferation of Internet of Things (IoT) devices introduces new cybersecurity challenges, as many IoT devices lack robust security controls and are vulnerable to exploitation. Attackers can compromise IoT devices to launch distributed denial-of-service (DDoS) attacks, infiltrate networks, or harvest sensitive data, posing risks to individuals and critical infrastructure.
- Supply Chain Attacks
Supply chain attacks target the interconnected ecosystem of vendors, suppliers, and service providers that support organizations’ operations. By infiltrating trusted third-party vendors or compromising software supply chains, attackers can inject malware, manipulate hardware components, or exploit vulnerabilities to compromise targeted organizations.
Proactive Solutions for Cybersecurity
- Robust Endpoint Security
Implementing robust endpoint security solutions, such as antivirus software, intrusion detection systems, and endpoint detection and response (EDR) tools, can help organizations detect and mitigate threats targeting endpoint devices, including laptops, desktops, and mobile devices.
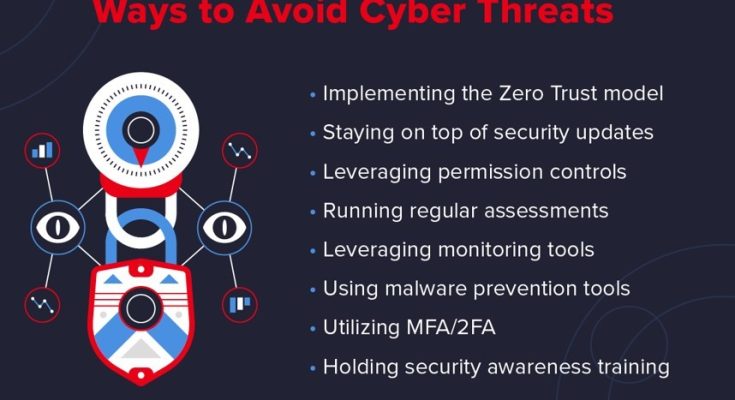
- Multi-Factor Authentication (MFA)
Deploying multi-factor authentication (MFA) mechanisms, such as biometric authentication, one-time passwords, or security tokens, can enhance authentication security and mitigate the risk of unauthorized access to sensitive systems and data.
- Security Awareness Training
Educating employees about cybersecurity best practices, such as identifying phishing emails, recognizing social engineering tactics, and safeguarding sensitive information, can empower them to recognize and mitigate cyber threats effectively.
- Network Segmentation
Implementing network segmentation strategies to partition networks into distinct zones with varying levels of trust can limit the lateral movement of attackers within network environments and contain the impact of potential security breaches.
- Incident Response and Cyber Resilience
In today’s rapidly evolving cyber threat landscape, organizations must prioritize incident response and cyber resilience to effectively combat cyber attacks and minimize the impact of security incidents. Incident response refers to the coordinated approach taken by organizations to detect, respond to, and recover from cybersecurity incidents, such as data breaches, malware infections, or network intrusions. On the other hand, cyber resilience encompasses a broader strategy aimed at building robust defenses, adapting to evolving threats, and maintaining business continuity in the face of adversity.
Effective incident response begins with proactive planning and preparation. Organizations must develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to various types of cyber incidents. These plans should include clear escalation paths, communication protocols, and predefined actions to contain and mitigate security breaches promptly. Regular training and tabletop exercises are essential to ensure that stakeholders are well-prepared to execute incident response procedures effectively when faced with a real-world cyber threat.
Cyber resilience goes beyond incident response by focusing on building a resilient infrastructure and organizational culture that can withstand and recover from cyber attacks. This involves implementing robust cybersecurity controls, such as network segmentation, encryption, and access controls, to mitigate the risk of cyber threats and limit their impact. Additionally, organizations should invest in technologies such as threat intelligence, security analytics, and continuous monitoring to detect and respond to threats in real-time, thereby enhancing their ability to adapt and respond to evolving cyber threats.
Furthermore, fostering a culture of cybersecurity awareness and accountability is critical to enhancing cyber resilience. Employees should be educated about cyber risks, trained on cybersecurity best practices, and encouraged to report suspicious activities promptly. By promoting a proactive approach to cybersecurity and empowering employees to play an active role in defense, organizations can strengthen their cyber resilience posture and minimize the likelihood and impact of cyber attacks.
Conclusion
As cyber threats continue to proliferate and evolve, organizations and individuals must remain vigilant and proactive in safeguarding their digital assets and infrastructure. By understanding the diverse landscape of cyber threats and implementing proactive cybersecurity solutions, organizations can mitigate risks, enhance resilience, and protect against the ever-present specter of cyber attacks. Together, we can fortify the digital frontier and foster a secure and resilient cyber landscape for all.